Risk actors are exploiting a zero-day vulnerability (CVE-2025-11371) in Gladinet CentreStack and Triofox merchandise, which permits a neighborhood attacker to entry system recordsdata with out authentication.
At the least three firms have been focused thus far. Though a patch will not be but obtainable, clients can apply mitigations.
CentreStack and Triofox are Gladinet’s enterprise options for file sharing and distant entry that enable utilizing an organization’s personal storage as a cloud. In accordance with the seller, CentreStack “is utilized by 1000’s of companies from over 49 international locations.”
No repair, all variations affected
The zero-day vulnerability CVE-2025-11371 is a Native File Inclusion (LFI) flaw affecting the default set up and configuration of each merchandise, impacting all variations together with the newest launch, 16.7.10368.56560.
Researchers at managed cybersecurity platform Huntress detected the safety subject on September 27 when a menace actor efficiently exploited it to acquire a machine key and execute code remotely.
A better evaluation revealed that the difficulty was an LFI leveraged to learn the Net.config and extract the machine key. This allowed the attacker to make use of an older deserialization vulnerability (CVE-2025-30406) and obtain distant code execution (RCE) by way of ViewState.
The CVE-2025-30406 deserialization bug in CentreStack and Triofox was additionally exploited within the wild in March, and was because of a hardcoded machine key. An attacker figuring out the important thing might carry out RCE on an affected system.
“After subsequent evaluation, Huntress found exploitation of an unauthenticated native file inclusion vulnerability (CVE-2025-11371) that allowed a menace actor to retrieve the machine key from the applying Net.config file to carry out distant code execution by way of the aforementioned ViewState deserialization vulnerability” – Huntress
Huntress contacted Gladinet to allow them to know the discovering. The seller confirmed that it was conscious of the vulnerability and mentioned that it was within the technique of notifying clients of a workaround till a patch is offered.
The researchers shared the mitigation with the focused buyer and revealed the next suggestions to guard towards CVE-2025-11371:
- Disable the temp handler within the Net.config file for the UploadDownloadProxy part at “C:Program Recordsdata (x86)Gladinet Cloud EnterpriseUploadDownloadProxyWeb.config”
- Find and take away the road that defines the temp handler — it factors to t.dn
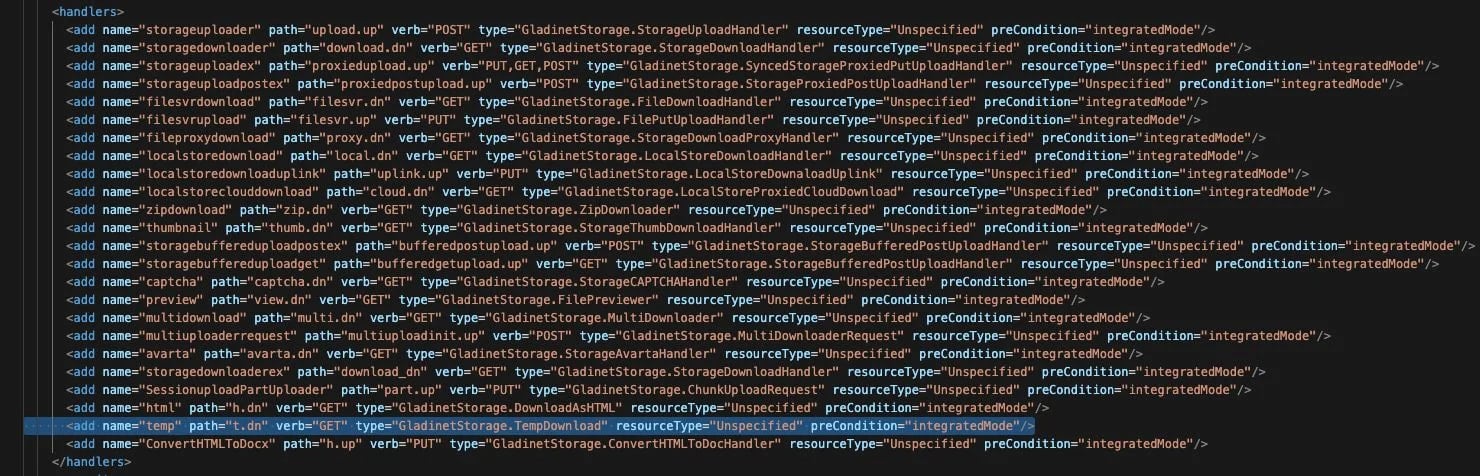
Supply: Huntress
This line permits the susceptible performance that attackers exploit by way of Native File Inclusion, so eradicating it prevents exploitation of CVE-2025-11371.
The researchers warn that the mitigations “will impression some performance of the platform,” however ensure that the vulnerability can’t be exploited.


